
24 Oct Clever phishing techniques: QR codes with ASCII and Blob URIs that bypass security
Learn how cybercriminals exploit QR codes.
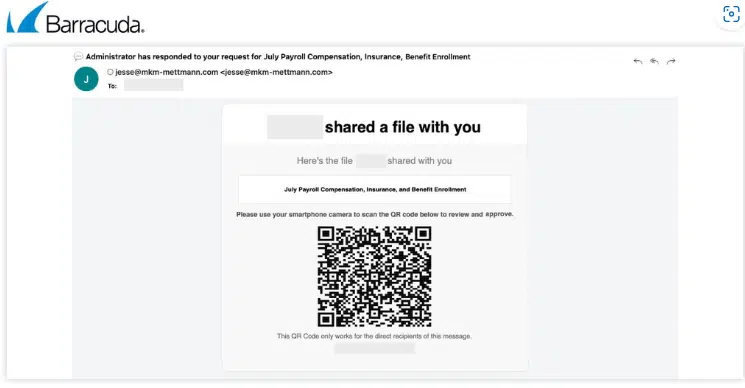
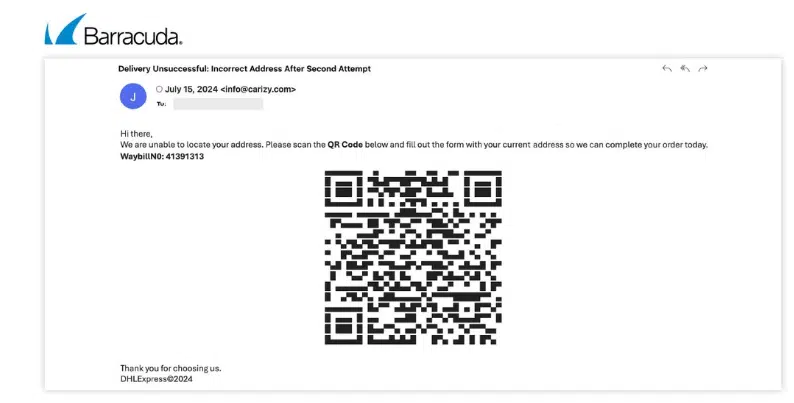
Example 2
In this case, the attacker impersonates the courier company DHL and asks the recipient to fill out a form after scanning the QR code. Upon scanning the code, the victim is unexpectedly redirected to a phishing site.
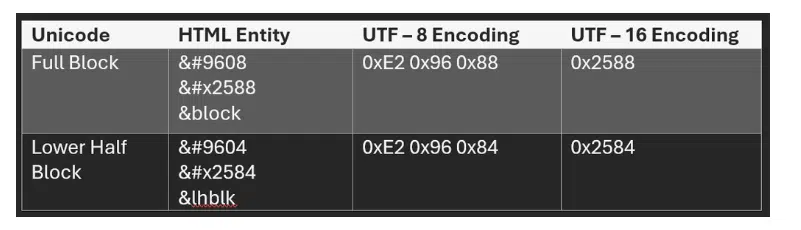
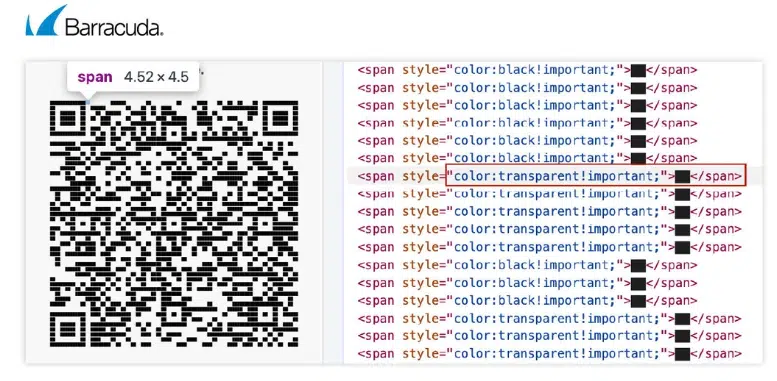
Another important point is that, in the case of HTML entities, each “block” can have multiple representations, and attackers can use single blocks or combinations of them to generate QR codes based on ASCII/Unicode.
All of this increases the possibilities for combinations, making ASCII-based QR codes particularly difficult to detect.
Barracuda highlights that if security technologies identify the potential use of ASCII QR codes in a phishing attack, one of the simplest solutions is to take a screenshot of the phishing email and pass it to an OCR engine to read the URL hidden behind the QR code.
The Vast Potential of Blob URI to Bypass Security Measures
Blob URIs (also known as Blob URLs or Object URLs) are used by browsers to represent binary data or file-like objects (called Blobs) that are temporarily stored in the browser’s memory.
Blob URIs allow web developers to work with binary data, such as images, videos, or files, without having to upload or download them from an external server.
Because Blob URIs don’t retrieve data from external URLs, traditional URL filtering and scanning tools may initially fail to recognize the content as malicious.
Cybercriminals create phishing pages using Blob URIs, hoping that detection systems will have a harder time identifying and blocking malicious content.
One of the first examples of a phishing attack using Blob URIs, identified by Barracuda’s threat analysts, involved impersonating Capital One, encouraging users to click “Check your account.” This redirected them to an intermediary phishing page that generated a Blob URI and quickly redirected the browser to the newly created address.
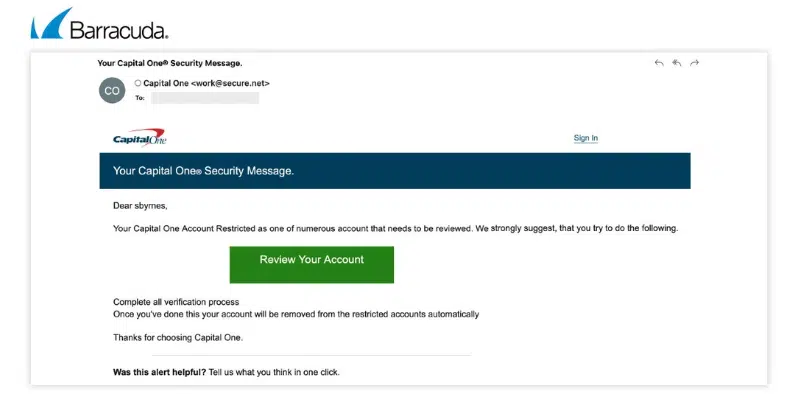
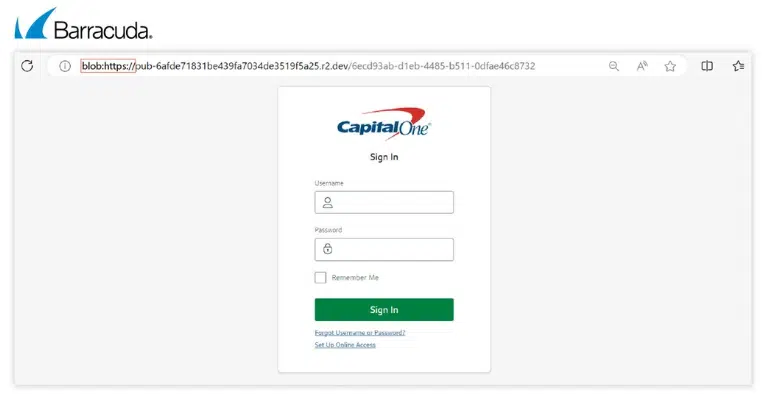
What does a Blob URI do?
It displays a fake Capital One login page to the victim.
Threat analysts, during various tests, also noticed that the Blob URI technique was used in phishing attacks impersonating Chase and Air Canada.
Summary
Phishing techniques to evade detection have evolved significantly, posing an increasing threat to organizations. Cybercriminals are constantly improving their methods to bypass traditional security measures. As phishing attacks become more sophisticated, it is essential to implement multilayered defense strategies and promote a strong security culture.
Megharaj Balaraddi, Associate Threat Analyst at Barracuda, also contributed to the research for this blog post. The original article can be found on the Barracuda Blog.

