08 Apr New methods of email cyberattacks – Barracuda Email Threat Radar Report
Together with Barracuda’s March Threat Review, which highlights the latest threats and how to defend against them, we invite you to read the full article:
In cybersecurity, one thing is certain – attackers never rest. This is confirmed by the latest Email Threat Radar report from Barracuda’s analysts, which sheds light on the newest phishing campaigns and extortion attempts targeting organizations around the world. In March 2025, three particularly interesting (and dangerous) threats were highlighted:
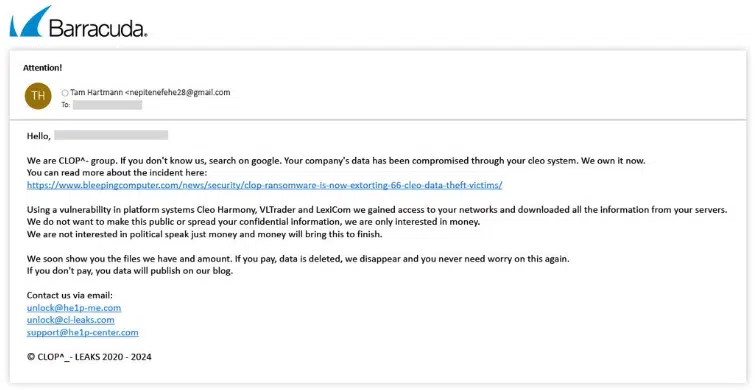
1. Impersonating Clop Ransomware – Extortion Without the Attack
Why go through the trouble of launching a real ransomware attack when you can simply pretend you did?
Cybercriminals have started sending emails impersonating the Clop group, threatening to leak “stolen” data allegedly obtained during a corporate network breach. To boost credibility, they refer to real news articles about past Clop attacks on users of Cleo platforms (such as Cleo Harmony or VLTrader).
These messages include contact addresses and an invitation to negotiate a “ransom,” although – interestingly – they lack a specific payment amount or typical elements of an actual ransomware attack (like encrypted chat links or strict response deadlines). It’s more manipulation and intimidation than a real breach.
What to watch for:
-
Threats of data leaks after a supposed breach
-
References to real-world news and incidents
-
Absence of classic ransomware indicators (no encryption, no ransom amount, no chat portal)
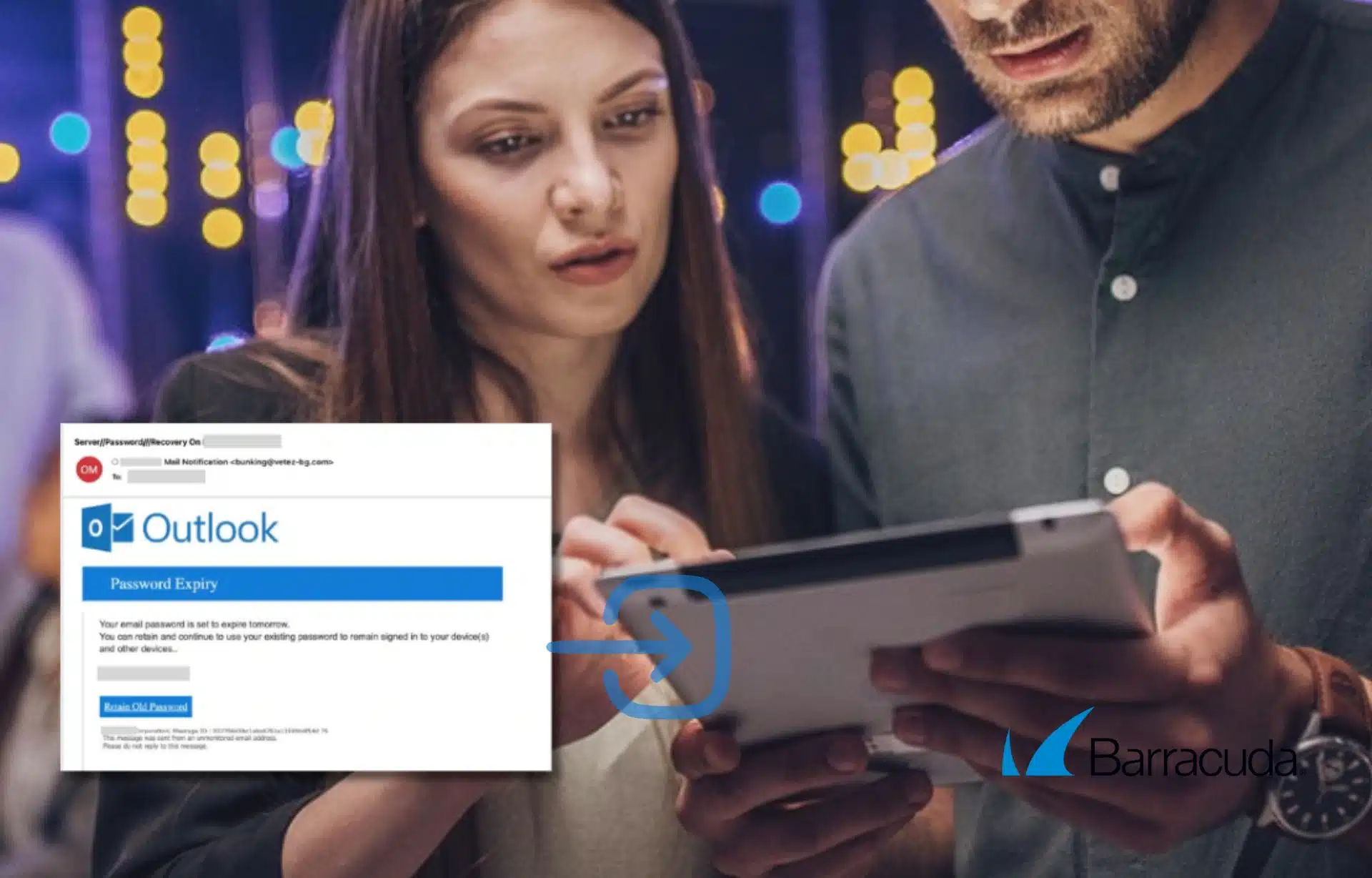
2. LogoKit – Phishing Taken to a New Level
LogoKit is a phishing platform that operates as a “phishing-as-a-service” (PhaaS). Active since 2022, it continues to evolve with new capabilities that make it difficult for traditional security tools to detect.
In the March campaign, cybercriminals sent emails with subject lines such as “Password Reset Requested” or “Immediate Account Action Required,” creating a sense of urgency to change a password. After clicking the link, the victim was taken to a fake login page created in real time, displaying the company’s logo dynamically pulled from sources like Clearbit or Google Favicon.
The most dangerous aspect? The fake page reacts in real time – as soon as the victim types in their credentials, the information is immediately captured by the attacker.
What to watch for:
-
Suspicious links containing the victim’s email address
-
Company logos loaded from external sources
-
Urgent messaging that pressures the user to act quickly

3. Phishing with SVG Files – Innocent Graphics, Serious Threat
As detection tools become more advanced, cybercriminals continue to look for new attack methods. One increasingly popular tactic involves phishing emails with SVG (Scalable Vector Graphics) file attachments.
SVG is a web-based vector image format that can contain embedded scripts which appear harmless to many security tools. In the cases analyzed by Barracuda, emails included only the attachment—no text—and clicking it led to a fake Microsoft login page or triggered the download of a malicious ZIP file.
Even more cleverly, if the attachment detects that it’s being opened in a sandbox environment (a controlled and secure testing space), it redirects the user to a legitimate shopping website – a trick designed to avoid detection.
What to watch for:
-
SVG files with clickable elements – do not open!
-
Redirects leading to downloads of other files
-
Unusual browser behavior, warnings, or alerts
How to Protect Yourself
The best defense is a combination of awareness and robust tools. Barracuda Email Protection offers comprehensive defense against such threats through:
-
Email Gateway Defense
-
Advanced phishing and spoofing detection
-
Impersonation Protection
-
Incident response and domain protection
-
Cloud backup and user awareness training
Thanks to integration with Microsoft 365 and the use of AI-driven analysis, Barracuda effectively neutralizes even the most advanced, targeted phishing campaigns.
Summary
Email attacks are becoming increasingly sophisticated — they mimic ransomware, impersonate login portals, and hide malicious scripts in graphics. What used to look suspicious is now often almost indistinguishable from legitimate communication.
That’s why it’s crucial for your company to be properly protected. If you’d like to learn more about how to secure your employees’ mailboxes effectively – get in touch with the Kappa Data team. We’ll help you choose and implement the right solutions before anything goes wrong.
Want to receive similar insights regularly?
Sign up for the Barracuda newsletter!

